So You Think Fgets is Safe?
Shellcrack
FLAG{REDACTED}
This was a simple, “run your shellcode” challenge. Use the buffer overflow to overwrite the return address with the address of your buffer. Since the address of the buffer is given to you, this one was pretty easy.
If there was one issue, it would be that there’s a canary. But since it does not show up on checksec, it is a user made canary. The fun part is that the canary leaks itself, because the buffer is copied to 0x20 bytes after the start of the actual buffer, and printed from there, leaking the canary which is right after. Brilliant.
- Since the fread, accepts only 0x10 bytes, we put in some random characters + a newline
- Read in the canary that was leaked
- Put the shellcode in the buffer, then proceed to jump to it and execute to pop a shell
cat flag
1 | #!/usr/bin/python3 |
Stack-dump2
FLAG{REDACTED}
stack-dump + aslr? ez
Thought this one would be harder. Building on the stack-dump from week 2, this time all I had to do extra was leak some addresses.
Although fgets is used, we specify the length, rendering it completely useless.
- Grab the pointer on the stack, it’s just one byte from the start of the buffer, so that’s great.
- Dump the canary by reading memory from the start of the canary, which is
0x69bytes from the useful pointer. - On reading the canary, the next step is finding where the
winfunction is. We do that by leaking another address on the stack, this time from the code section. (Just in case the offsets for the code part and the stack are different) - Use the code pointer to find the address of the
winfunction - Find the padding before and after the canary and overflow, to jump to the win function.
cat flag
1 | #!/usr/bin/python3 |
Image-viewer
FLAG{REDACTED}
The effect of an unchecked atoi can be so intense lol
This was a very interesting exploit. Since the buffer and the images array both are global variables, and the atoi is directly used to index into the array, it can be used to index into the buffer, using negative indices. Pretty cool. All you need to be careful is of byte alignment.
- First you need the index. I chose -2, but -1 would also work the same. Put this index at the start of the buffer, so you can pass that to atoi.
- Choose your filename. The whole idea is that you can read any file you want, so choose the name, and put it right after the index (although it can be mostly anywhere in the buffer). Remember that the “blacklist” was for the exact file name, so it is easy to get around by simply supplying a relative path like
./flaginstead offlag. - Find the address of the filename string. In my case, it was
0x804c064, although there was no need to worry about byte alignment for the filename. - Padding the buffer with a bunch of ‘a’s, the next thing on the list is memory management.
- Make sure that the “entry” into the images array seems legitimate, we use the first 4 bytes to store the id, which based on the checks should be the same as the array index, -2 in this case. The next 4 bytes store the address to the filename. You need to worry about byte alignment for the index to be correct, so “allocating memory” for the images array from the end of the buffer is a great idea.
- You can now leak any file you want :)
1 | #!/usr/bin/python3 |
Reversing: Chal.jpg
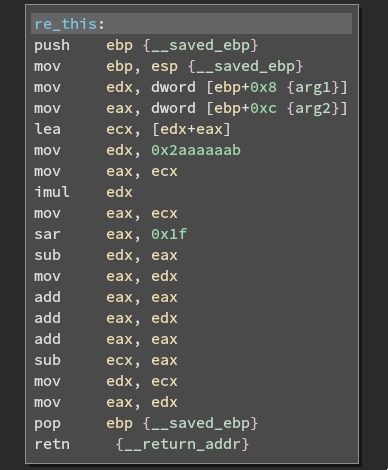
The magic numbers really threw me off
My only thought when this compiled to something very close to the image was, “Why is it that simple!? “
So I looked into it a bit more. I believe here’s what the mod operation does (atleast in C)
- Use the “magic number”, in this case
0x2aaaaaab, integer multiply with the sum of the two arguments. - Then get the top bit of the number. If the number is negative (top bit is 1), it would then subtract it from the product calculated in 1.
- Now I call it the “magic number”, because somehow at this point it has the calculated the largest number that when multiplied by 6 (the number that the sum is modded by) gives the largest number less than the sum. For example, if
(arg1 + arg2) == 13then the calculated number is2. And2 * 6 == 12is the largest multiple of6less than13 - The triple
addinstructions are simply multiplying the number calculated in (3) by6. - Then it subtracts the largest multiple from the sum and returns the remainder.
- I also checked out odd number mods and that shifts the number to the right by
1before shifting it back by2. hmmmmm - It also becomes very different when I optimize using the
-O2flag.
1 | int re_this(int arg1, int arg2) { |
Source Code Auditing: source.c
source.c
There were three two and a half (??) vulnerabilites that were found in the source code.
The first one was a format string vulnerability on lines 142-146. Although snprintf is used, and a constant length is given to the function, the format is left to the user. Brilliant.
- This lets me dump the whole stack if I want into the syslog (which can be used through the next vulnerability) or write to anywhere in the program, (perhaps the GOT?) letting me gain some RCE :)
1 | char log[MAX_LEN]; |
The next one was an overlook? but the admin_level is set to a default of 0 which means any user that connects to the server is automatically admin. GG.
- That essentially lets me run any commands on the server. If I can run another vulnerable program, maybe I can do a privilege escalation to get root privileges yay!
- I could also use the vuln (1) to then send the dumped data from syslog over to my server for further exploitation of the server. (but I wouldn’t need to)
The issue was on line 140:
1 | uint8_t admin_level = 0; |
When the program is so broken that even the exploit doesn’t work.
This third one I thought was a vulnerability, but it is more a vulnerability in the making. The switch statement in the SET_PERMISSION_LEVEL sets the admin_level, which is an unsigned 8-bit integer to the value of level, which is a 32-bit integer.
- That would allow the user to easily overflow the value of
admin_levelto zero by settinglevelto a multiple of256. - However, this does not work in practice as the
sscanfwill never succeed in reading anything, because the first character ofactionarray is never discarded by the program, nor does it allow the user to enter more characters. So if the user enteredUto execute theSET_PERMISSION_LEVELcase, it wouldn’t be able to read inUinto level, and it would set theadmin_levelto-1. - There is also no break statement after the
SET_PERMISSION_LEVELcase, so if the command runner (T) was ever a blocked command, you could run it using (U) which should only set permissions, but not really. - So while this is not a vulnerability right now, it will be one when the developer gets the
SET_PERMISSION_LEVELcase to work as intended. Which is something to look out for
The broken code in question:
1 | uint8_t admin_level = 0; |
Conclusion
This was an interesting week, because while the challenges were easier than last week in general, with the exception of shellcrack all the programs used fgets to run a buffer overflow instead of gets. It is important to make sure I don’t discard fgets as a point of attack in the future just because it is fgets and a length is passed in so there is no way that I can exploit it.
Nonetheless, was fun exploiting.